Web application firewall – Configuring Load Balancing
Web application firewall
The web application firewall (WAF) is a specialized service that caters to protecting web-based traffic to protect from vulnerabilities and exploits. The service is based onthe Core Rule Set (CRS) developed by the Open Web Application Security Project (OWASP).The service is easy to implement and requires no modification of your application code to be functional, and it works in line with your traffic. All alerts raised will be logged in the WAF log, which is integrated into Azure Monitor. You can customize rules based on your requirements and against several sites served by the Application Gateway.
Top Tip
You can protect up to 40 websites using the WAF service per Application
Gateway instance.
There are several protections the service caters to, including the following:
- Protection against HTTP protocol violations and anomalies
- SQL injection attacks
- Cross-site scripting (XSS) attacks
- Geo traffic filtering (allow/block regions from accessing your applications)
The following diagram is an illustration of the WAF service in action:
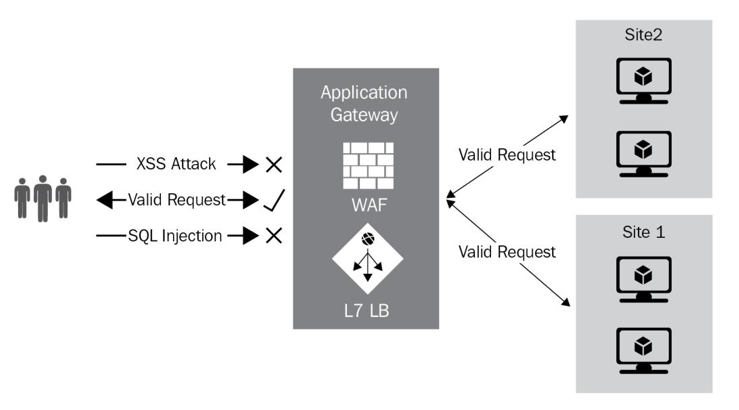
Figure 16.2 – URL path-based routing
Now that you understand more about the load balancing services available to you in Azure, we will explore each of these services in a bit more detail and explore the configuration of each of these.
Azure Load Balancer
Azure Load Balancer is a load balancer that operates at the transport layer (Layer 4 in the OSI network reference stack). Azure Load Balancer supports the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), and it can be used to load-balancetraffic to yourapplications and is generally used in scenarios where you would like to enable HA. The concept of HA refers to the ability of your applications or services to sustain some form of downtime; should you sustain a loss of a workload or node, your load balancer will redirect traffic to the remaining available and functional workloads or nodes. Load balancers provide scalability by sharing the load of the traffic among several responding servers, which also creates resiliency as traffic is not dependent on a single node to respond. Azure load balancers provide high throughput and low latency and can scale up to millions of flows. They support various inbound and outbound scenarios.
The Azure Load Balancer service can be used for the following:
- Public load balancer: Incoming internet traffic is load-balanced to VMs.
- ILB: Traffic can be load-balanced across VMs inside a virtual network. You can also use it in a hybrid scenario, where it reaches a load balancer inside an on-premises network.
- Port forwarding: You can forward traffic to specific ports on specific VMs using inbound network address translation (NAT) rules.
- Outbound connectivity: You can also provide outbound connectivity for VMs inside a virtual network using it on Azure Load Balancer as a public load balancer.
Top Tip
Whenever you hear a reference to HA or scalability, you should immediately start to question whether a load balancer should be implemented; in many scenarios, this will be one of the resources you will need in your toolset.
Now that you understand a bit about what load balancing is and, more specifically, what Azure Load Balancer is, we will explore some of the features and capabilities it provides.